Secure Remote IoT P2P On Windows 10: A Comprehensive Guide
In this rapidly evolving digital landscape, where the Internet of Things (IoT) is no longer a futuristic concept but a present-day reality, is it possible to securely harness the power of remote IoT devices via peer-to-peer (P2P) connections on Windows 10? The answer, reassuringly, is yes. But it demands a vigilant approach to security.
The architecture of connecting remote IoT devices, especially in a P2P network, can seem complex at first glance. The core challenge revolves around ensuring that the communication channels remain both private and authenticated. This necessitates a deep understanding of the best practices, the appropriate tools, and the necessary configurations required to establish a robust and secure connection. With the proliferation of IoT devices, from smart home appliances to industrial sensors, the need to protect the data they generate and transmit has never been more critical. The following text breaks down the steps to enable remote IoT P2P SSH connections on Windows 10, with emphasis on security.
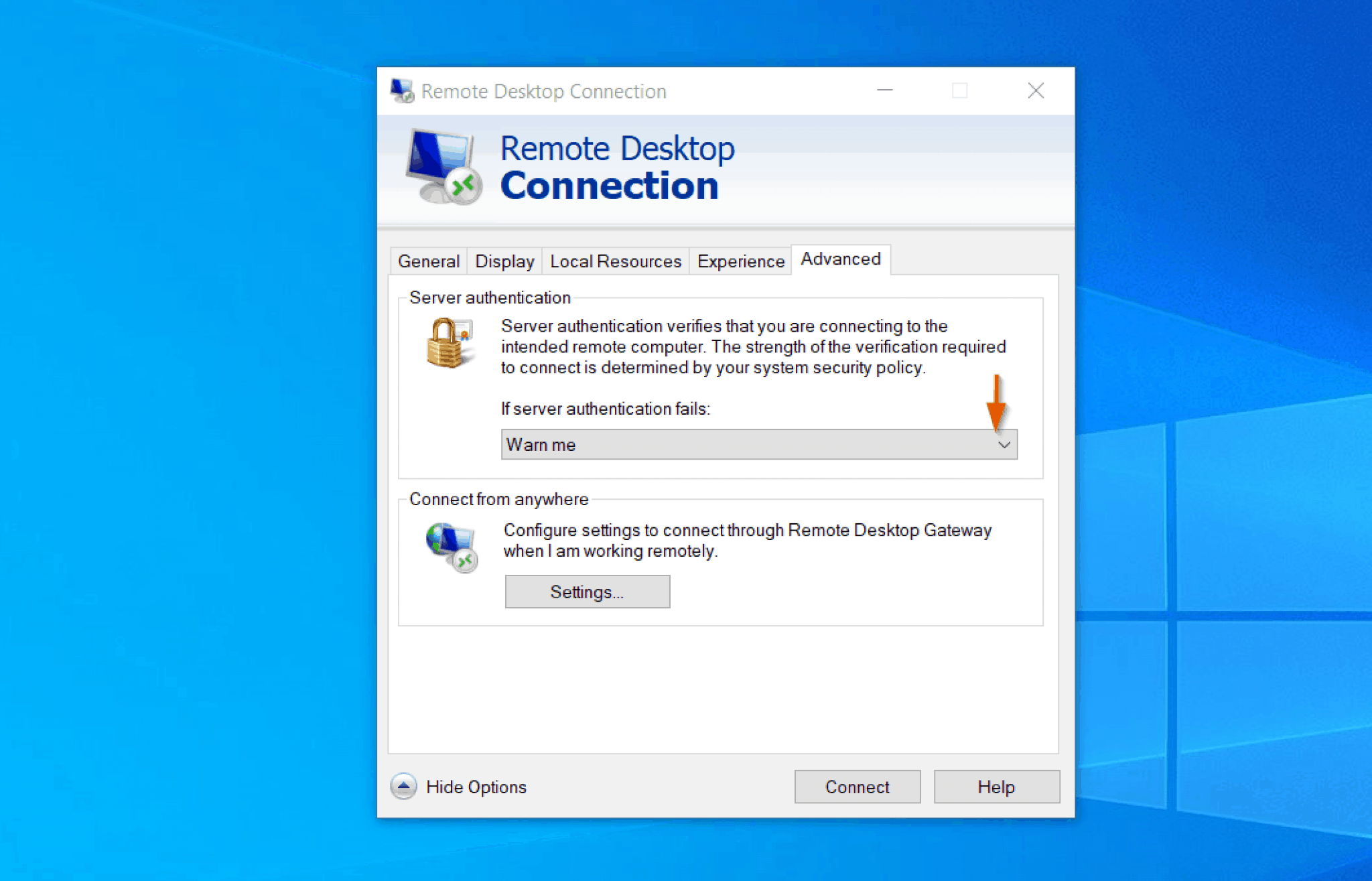
One of the primary methods to accomplish this is by using Secure Shell (SSH) protocol. SSH provides a secure channel over which data can be transmitted, mitigating the risk of eavesdropping or unauthorized access. Utilizing SSH necessitates the configuration of an SSH server on the target device, in addition to the client on the Windows 10 machine.
The gateway to achieving secure remote IoT P2P connections on Windows 10 begins with a critical first step: downloading and installing the appropriate software client on your Windows 10 machine. For many solutions, this will involve obtaining the client from the official website. This client software serves as the initial point of contact, effectively acting as the bridge between your local device and the remote IoT device. The selection of the right client is paramount; always ensure the software comes from a trusted source to minimize the risk of malware or other malicious software.
Once the client is installed, the subsequent phase involves configuring the security settings. This is where the true power of a secure P2P connection lies. This includes setting up encryption protocols, authentication mechanisms, and access control measures. Such mechanisms safeguard the sensitive data that is exchanged between the devices. In practical terms, this can involve setting up encryption to protect the data's confidentiality, choosing strong authentication methods to verify the identity of connecting devices, and configuring access control lists to restrict which devices or users have the ability to communicate.
To securely connect remote IoT devices in a P2P network, several methods and protocols can be employed. These include encryption, authentication, and access control mechanisms that help protect sensitive data and ensure authorized access. Implementing such methods is crucial for ensuring that only legitimate users and devices can access the network.
The role of SSH in the ecosystem is invaluable. It provides a secure, encrypted channel over which data can be transmitted, thus mitigating the risks of eavesdropping, data tampering, and unauthorized access. Configuring the SSH server on the remote IoT device and the corresponding client on your Windows 10 machine is an essential part of the process.
Once you've set up the software and configured the security settings, the final step is to test the connection meticulously. This testing phase is not merely a perfunctory step; it is a critical part of the process, ensuring that everything functions as intended. This involves verifying that you can successfully establish a connection, transfer data securely, and that all security protocols are functioning correctly. This is where you can ensure that the safeguards you've put in place are working as expected.
The installation phase is often the starting point. It involves finding and installing the software. Ensure you download from official, trustworthy sources to avoid potential security risks. Once installed, the configuration phase takes over. This involves tweaking settings, setting security parameters, and potentially customizing the client software to meet specific requirements.
With Windows 10 being one of the most widely used operating systems, users are looking for reliable solutions to download and set up secure connections without incurring unnecessary costs. In this context, the search for "free" secure P2P solutions is a recurring theme. Users should approach such searches with caution and prioritize solutions that offer robust security features even if they are free. Free solutions can sometimes be an excellent option, but always verify the security reputation of the provider.
In today's interconnected world, securely connecting remote IoT devices in a P2P environment on Windows 10 has evolved from a convenience to a necessity. Whether you're a tech enthusiast, a business professional, or an individual looking to manage your smart home devices, the ability to establish secure connections is paramount.
The benefits of securing these connections are manifold. First and foremost, secure connections protect your data from unauthorized access. Secondly, they protect the integrity of your system, ensuring that remote devices are not compromised. Finally, secure connections provide peace of mind, knowing that your network and devices are safeguarded against potential threats.
Beyond Windows 10, other operating systems such as Raspberry Pi are frequently used in the IoT realm. This involves configuring SSH, security settings, and testing the connection. This method provides a direct and secure way to connect to your Raspberry Pi devices, enabling remote access and control.
Securely connecting remote IoT devices requires a multi-faceted approach. Start by downloading and installing the necessary client on your Windows 10 device. Then, delve into security configurations, including choosing strong encryption methods, robust authentication protocols, and access control mechanisms. Finally, test the connection thoroughly to ensure that everything functions as intended. Following this systematic method will help you to create a secure and reliable P2P connection.
If you're looking to securely connect remote IoT devices through P2P connections, this is an important step to follow. It is essential that you are vigilant about the software you download, the security protocols you implement, and the connections you test. The ability to securely and efficiently manage remote IoT devices is a critical skill in today's increasingly interconnected world.
Mastering remoteiot vpc ssh on Raspberry Pi and downloading files enhances your IoT capabilities significantly. Understanding the process of securely connecting a Raspberry Pi to AWS VPC using remoteiot is crucial.
In an era of interconnected devices, the skill to securely connect remote IoT devices is critical for professionals and tech enthusiasts alike. This involves configuring software, setting up security, and testing connections to make them secure and stable.